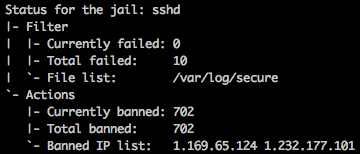
iptables
unban ip
List entries with line numbers
iptables -L -v --line-numbers
Delete entry
iptables -D name_of_chain number_of_line_with_IP_that_you_want_to_delete
Let’s imagine that we want to unban 91.194.16.60! chain name is ‘f2b-sshd‘ and line number is 10!

iptables -D f2b-sshd 10
Ban entire subnet
Example (banning some chinese sh*t)
iptables -A INPUT -s 119.249.54.0/24 -j DROP iptables -A INPUT -s 121.18.238.0/24 -j DROP